IAESONLINEIAESONLINE
Indonesian Journal of Electrical Engineering and Informatics (IJEEI)Indonesian Journal of Electrical Engineering and Informatics (IJEEI)Intrusion Detection Systems (IDS) are essential for maintaining the security of cloud computing environments, which are increasingly targeted by sophisticated cyber-attacks. This paper presents a novel hybrid approach for intrusion detection in cloud environments, combining Random Forest for feature selection, Long Short-Term Memory (LSTM) networks for temporal pattern recognition, and Transformer networks for contextual learning. Evaluated on CICIDS2017 and CSE-CIC-IDS2018 datasets, the proposed approach achieved weighted F1-scores of 97% and 99% respectively, significantly outperforming baseline models. The hybrid model improved accuracy from 95.1% to 98.0% and F1-score from 94.2% to 97.0% compared to LSTM-only approaches. While excelling at detecting common attack patterns such as Distributed Denial of Services (DDoS), challenges remain in identifying rare threats including SQL Injection. This research contributes to cloud security advancement by demonstrating the effectiveness of hybrid machine learning architectures in addressing the unique challenges of intrusion detection in distributed cloud infrastructures.
The hybrid model demonstrated strong overall performance in detecting common attack types such as DoS, DDoS, and brute force attempts.However, challenges remain in identifying rare and sophisticated attack types, particularly SQL Injection, Web Attacks, and Infiltration.This highlights a fundamental challenge in intrusion detection research.The model maintains sufficient efficiency for real-time monitoring in practical deployment scenarios, processing approximately 5,000 flows per second on standard hardware.
Berdasarkan penelitian ini, beberapa saran penelitian lanjutan dapat diajukan. Pertama, perlu dilakukan pengembangan model yang lebih baik dalam mendeteksi serangan yang jarang terjadi (rare attacks) seperti SQL Injection dan Web Attacks. Hal ini dapat dicapai dengan menggunakan teknik data augmentation atau transfer learning untuk meningkatkan representasi data serangan tersebut. Kedua, penelitian dapat difokuskan pada peningkatan interpretasi model deep learning, sehingga dapat dipahami alasan di balik keputusan klasifikasi yang diambil. Teknik Explainable AI (XAI) dapat diterapkan untuk memberikan wawasan yang lebih jelas tentang bagaimana model bekerja. Ketiga, penelitian dapat mengeksplorasi integrasi dengan threat intelligence feeds untuk meningkatkan kemampuan model dalam mendeteksi serangan baru dan yang belum pernah terjadi sebelumnya. Dengan menggabungkan informasi dari berbagai sumber, model dapat lebih adaptif dan responsif terhadap ancaman yang terus berkembang.
- Enhancing Intrusion Detection Systems in Cloud Computing Environments: A Hybrid Machine Learning Approach... doi.org/10.52549/ijeei.v13i3.6713Enhancing Intrusion Detection Systems in Cloud Computing Environments A Hybrid Machine Learning Approach doi 10 52549 ijeei v13i3 6713
- RID-Cloud: Spectral Recurrent Neural Network-Based Intrusion Detection in Cloud Environment: IETE Journal... doi.org/10.1080/03772063.2024.2428740RID Cloud Spectral Recurrent Neural Network Based Intrusion Detection in Cloud Environment IETE Journal doi 10 1080 03772063 2024 2428740
- An Advanced Neural Network Framework for Intrusion Detection | Research Square. advanced neural network... doi.org/10.21203/rs.3.rs-4043594/v1An Advanced Neural Network Framework for Intrusion Detection Research Square advanced neural network doi 10 21203 rs 3 rs 4043594 v1
| File size | 699.68 KB |
| Pages | 11 |
| Short Link | https://juris.id/p-3qE |
| Lookup Links | Google ScholarGoogle Scholar, Semantic ScholarSemantic Scholar, CORE.ac.ukCORE.ac.uk, WorldcatWorldcat, ZenodoZenodo, Research GateResearch Gate, Academia.eduAcademia.edu, OpenAlexOpenAlex, Hollis HarvardHollis Harvard |
| DMCA | Report |
Related /
UBHINUSUBHINUS Sistem ini mampu memberikan rekomendasi kondisi optimal air berdasarkan data yang diinputkan. Implementasi sistem ini berpotensi meningkatkan efisiensiSistem ini mampu memberikan rekomendasi kondisi optimal air berdasarkan data yang diinputkan. Implementasi sistem ini berpotensi meningkatkan efisiensi
UNIPEMUNIPEM Proses ini seringkali dilakukan secara subjektif tanpa pertimbangan berbasis data yang memadai. Penelitian ini bertujuan mengimplementasi dan mengembangkanProses ini seringkali dilakukan secara subjektif tanpa pertimbangan berbasis data yang memadai. Penelitian ini bertujuan mengimplementasi dan mengembangkan
ITSITS Data sensor dimanfaatkan untuk mengidentifikasi gejala awal kegagalan. Untuk menangkap ketergantungan temporal dan sekuensial dalam data deret waktu, kamiData sensor dimanfaatkan untuk mengidentifikasi gejala awal kegagalan. Untuk menangkap ketergantungan temporal dan sekuensial dalam data deret waktu, kami
UBHARAUBHARA Penelitian ini menunjukkan bahwa penanganan ketidakseimbangan kelas dengan SMOTE secara signifikan meningkatkan kinerja model klasifikasi kesehatan mental.Penelitian ini menunjukkan bahwa penanganan ketidakseimbangan kelas dengan SMOTE secara signifikan meningkatkan kinerja model klasifikasi kesehatan mental.
UBHINUSUBHINUS Sistem dibangun dengan tidak membuat kriteria yang statis. Kriteria dapat diubah sesuai kasus yang diinginkan. Namun, didalam sistem terdapat riwayat yangSistem dibangun dengan tidak membuat kriteria yang statis. Kriteria dapat diubah sesuai kasus yang diinginkan. Namun, didalam sistem terdapat riwayat yang
UBHINUSUBHINUS Semua perubahan termasuk pembaruan data, penghapusan kategori, modifikasi kata sandi, dan visualisasi grafik keuangan tersimpan dan tercermin secara akuratSemua perubahan termasuk pembaruan data, penghapusan kategori, modifikasi kata sandi, dan visualisasi grafik keuangan tersimpan dan tercermin secara akurat
STMISTMI Selain itu, pencatatan kegiatan serta pembuatan laporan lean maintenance pada seksi machining dan MTC masih menggunakan Microsoft Excel. Solusi untuk mengatasiSelain itu, pencatatan kegiatan serta pembuatan laporan lean maintenance pada seksi machining dan MTC masih menggunakan Microsoft Excel. Solusi untuk mengatasi
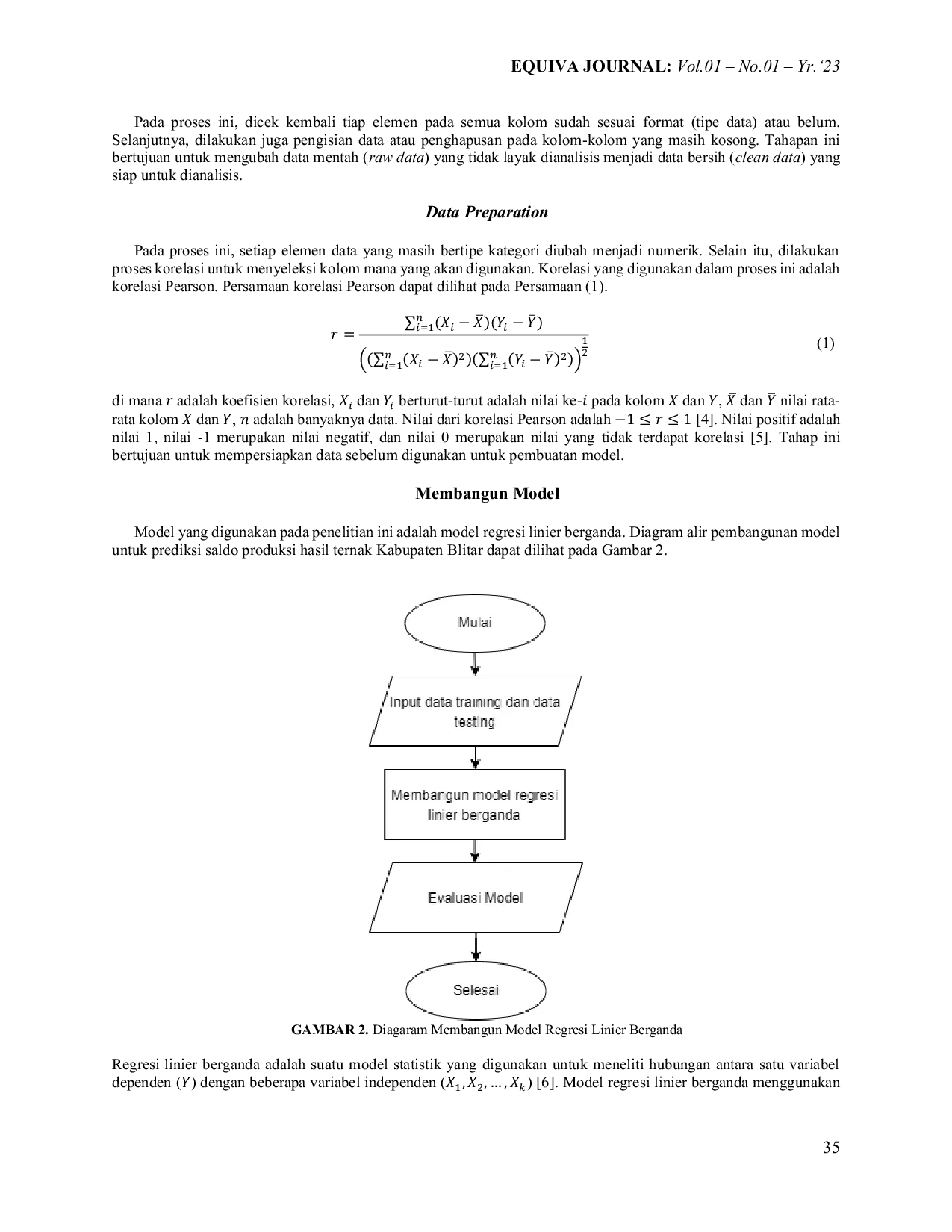
ITKITK Model regresi linier berganda dengan pembagian data training dan testing sebesar 85%. 15% menghasilkan akurasi terbaik, ditunjukkan oleh nilai MAE sebesarModel regresi linier berganda dengan pembagian data training dan testing sebesar 85%. 15% menghasilkan akurasi terbaik, ditunjukkan oleh nilai MAE sebesar
Useful /
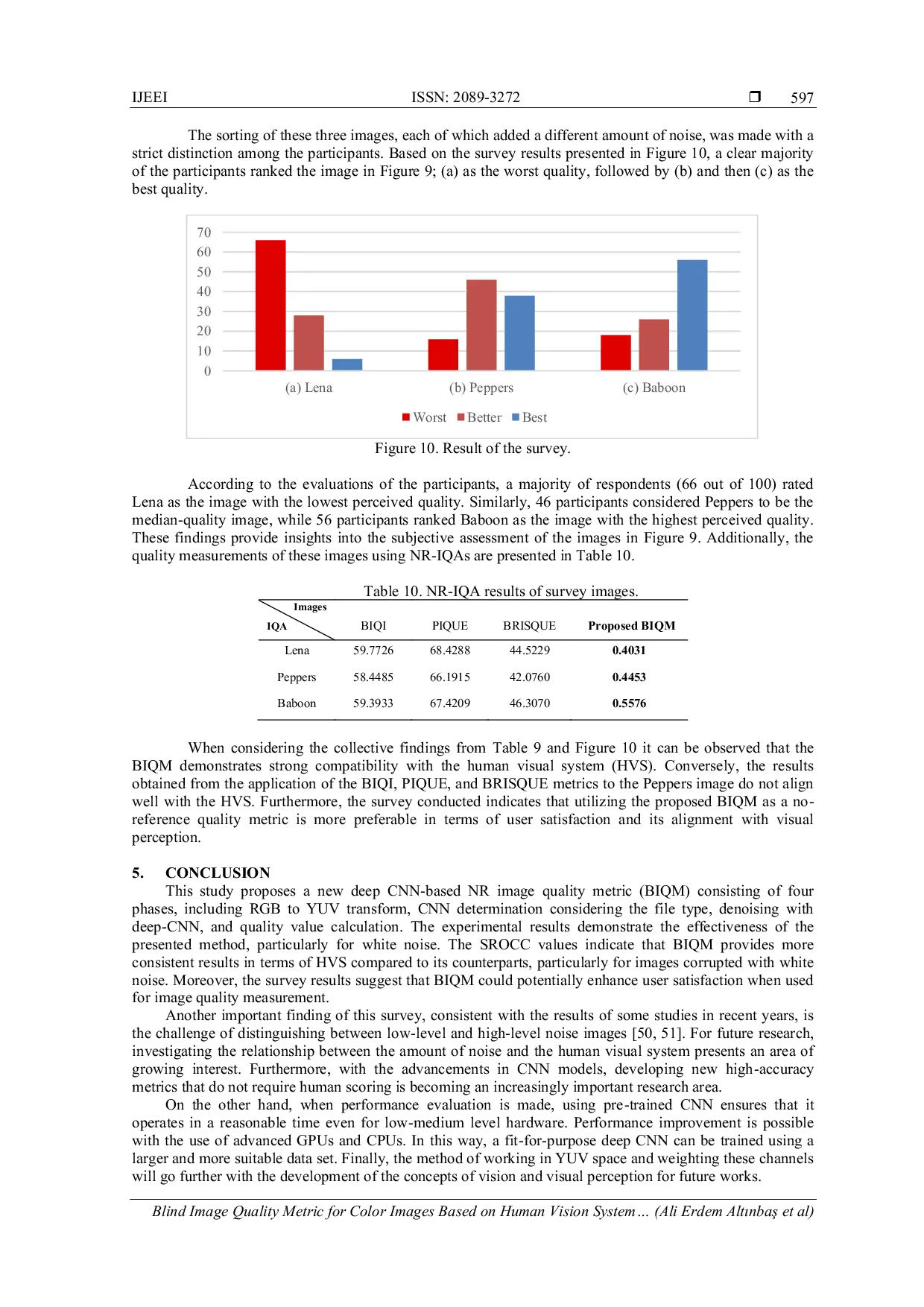
IAESONLINEIAESONLINE The SROCC values indicate that BIQM provides more consistent results in terms of HVS compared to its counterparts, particularly for images corrupted withThe SROCC values indicate that BIQM provides more consistent results in terms of HVS compared to its counterparts, particularly for images corrupted with
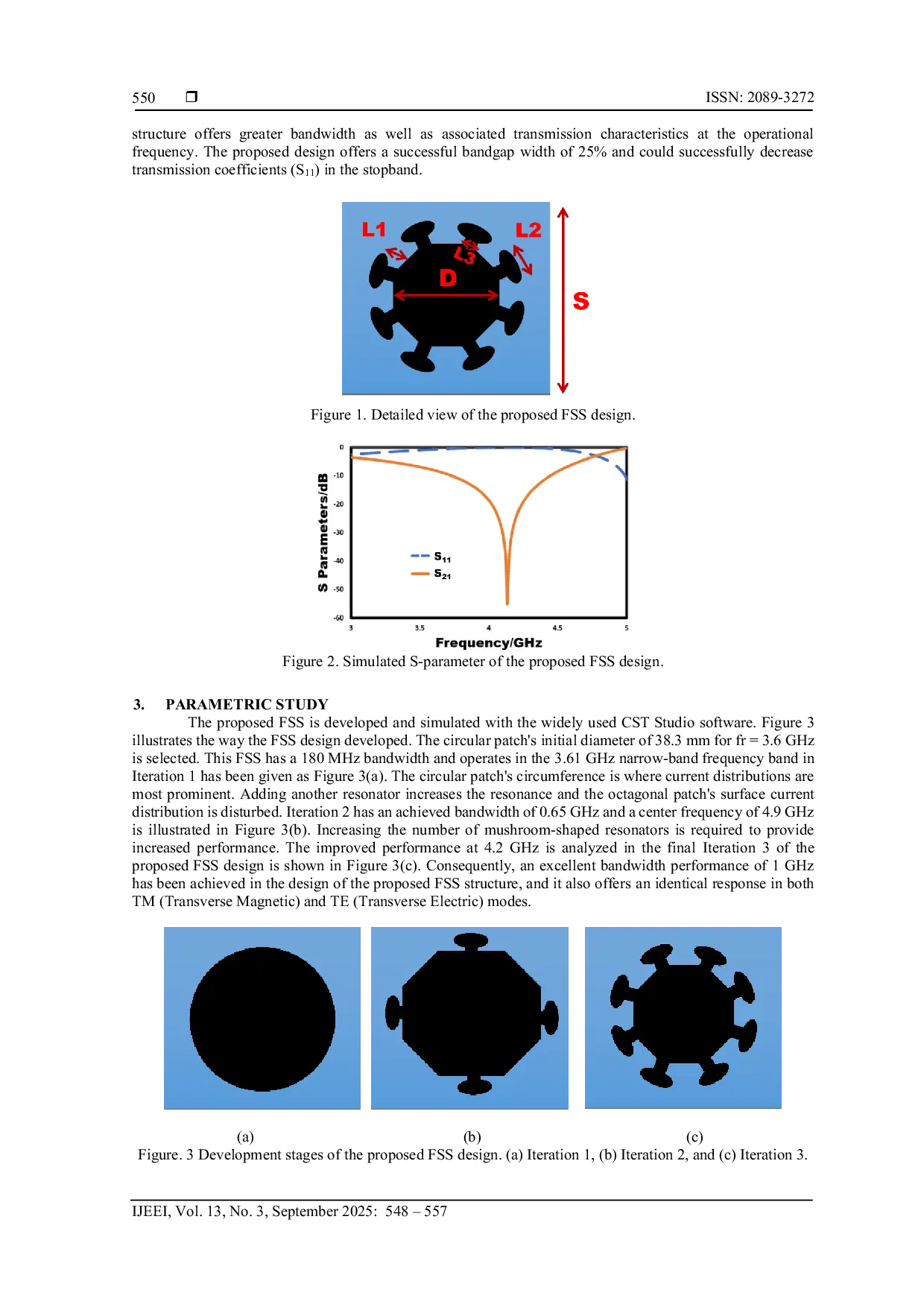
IAESONLINEIAESONLINE The proposed modified octagonal-shaped FSS demonstrates strong performance for 5G communication at frequencies below 6 GHz. The compact size, angular stabilityThe proposed modified octagonal-shaped FSS demonstrates strong performance for 5G communication at frequencies below 6 GHz. The compact size, angular stability
STMISTMI Sistem informasi ini juga meningkatkan efisiensi operasional karena operator dapat mencatat data assembly secara antarmuka sehingga mengurangi risiko kesalahanSistem informasi ini juga meningkatkan efisiensi operasional karena operator dapat mencatat data assembly secara antarmuka sehingga mengurangi risiko kesalahan
UNIKOMUNIKOM Penelitian ini bertujuan untuk mengetahui ketersediaan sarana pendidikan yang tersedia dan yang dapat diajangkau oleh penduduk yang tinggal di sekitarPenelitian ini bertujuan untuk mengetahui ketersediaan sarana pendidikan yang tersedia dan yang dapat diajangkau oleh penduduk yang tinggal di sekitar